 reader comments
reader comments
8 with 7 posters participating
Over the weekend, word emerged that a hacker breached far-right social media website Gab and downloaded 70 gigabytes of data by exploiting a garden-variety security flaw known as an SQL injection. A quick review of Gab’s open source code shows that the critical vulnerability—or at least one very much like it—was introduced by the company’s chief technology officer.
The change, which in the parlance of software development is known as a “git commit,” was made sometime in February from the account of Fosco Marotto, a former Facebook software engineer who in November became Gab’s CTO. On Monday, Gab removed the git commit from its website. Below is an image showing the February software change, as shown from a site that provides saved commit snapshots. 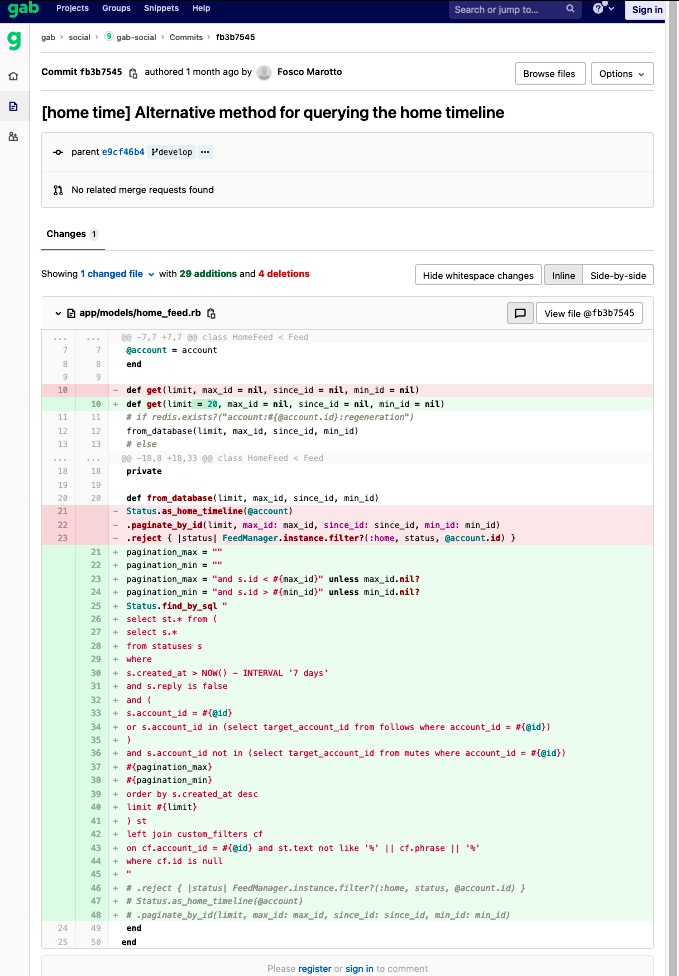
The commit shows a software developer using the name Fosco Marotto introducing precisely the type of rookie mistake that could lead to the kind of breach reported this weekend. Specifically, line 23 strips the code of “reject” and “filter,” which are API functions that implement programming idioms that protect against SQL injection attacks.
Developers: Sanitize user input
These idioms “sanitize” the inputs that website visitors enter into search boxes and other web fields to ensure that any malicious commands are stripped out before the text is passed to backend servers. In their place, the developer added a call to the Rails function that contains the “find_by_sql” method, which accepts unsanitized inputs directly in a query string. Rails is a widely used website development toolkit.
“Sadly Rails documentation doesn’t warn you about this pitfall, but if you know anything at all about using SQL databases in web applications, you’d have heard of SQL injection, and it’s not hard to come across warnings that find_by_sql method is not safe,” Dmitry Borodaenko, a former production engineer at Facebook who brought the commit to my attention wrote in an email. “It is not 100% confirmed that this is the vulnerability that was used in the Gab data breach, but it definitely could have been, and this code change is reverted in the most recent commit that was present in their GitLab repository before they took it offline.”
Affero General Public License, which governs Gab’s reuse of Mastodon, an open source software package for hosting social networking platforms.
Critics say the removal violates terms that require forked source code be directly linked from the site. The requirements are intended to provide transparency and to allow other open source developers to benefit from the work of their peers at Gab.
Gab had long provided commits at https://code.gab.com/. Then, on Monday, the site suddenly removed all commits—including the ones that created and then fixed the critical SQL injection vulnerability. In their place, Gab provided source code in the form of a Zip archive file that was protected by the password “JesusChristIsKingTrumpWonTheElection” (minus the quotation marks).
Representatives from the Mastodon project didn’t immediately respond to an email asking if they shared the critics’ concerns.
Besides questions about secure coding and license compliance, the Gab git commits also appear to show company developers struggling to fix their vulnerable code. The image below shows someone using the username “developer” trying unsuccessfully to fully fix the code containing the SQL injection vulnerability.
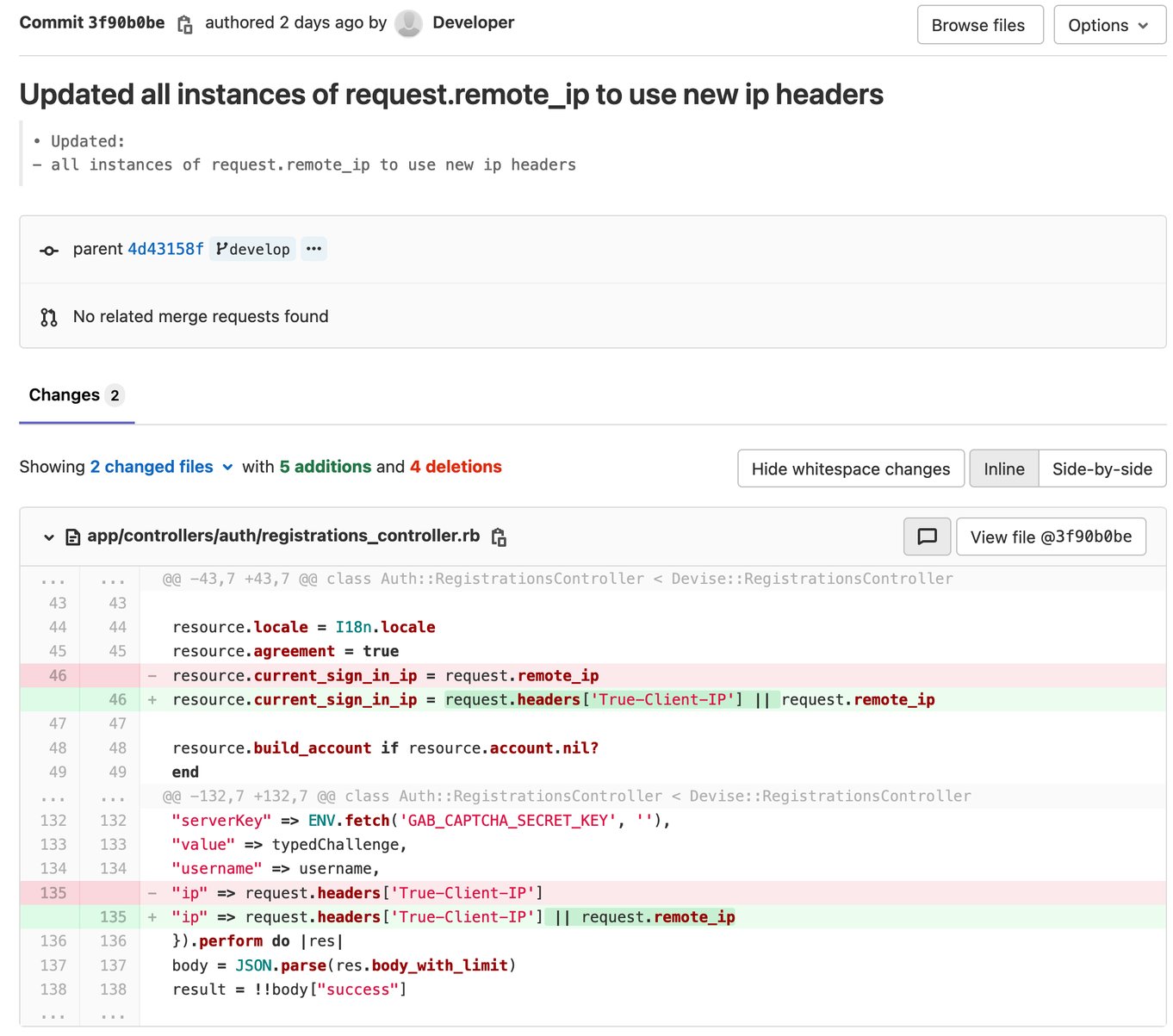
Thread participants respond by sarcastically pointing out the difficulty the developer seemed to be having.
Gab’s security breach and behind-the-scenes handling of code before and after the incident provide a case study for developers on how not to maintain the security and code transparency of a website. The lesson is all the more weighty given that the submission used the account of Gab’s CTO, who among all people should have known better.





