 reader comments
reader comments
46 with 37 posters participating, including story author
Still smarting from last month’s dump of phone numbers belonging to 500 million Facebook users, the social media giant has a new privacy crisis to contend with: a tool that, on a mass scale, links the Facebook accounts associated with email addresses, even when users choose settings to keep them from being public.
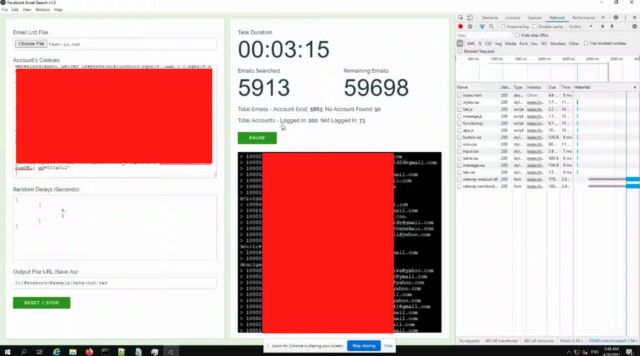
A video circulating on Tuesday showed a researcher demonstrating a tool named Facebook Email Search v1.0, which he said could link Facebook accounts to as many as 5 million email addresses per day. The researcher—who said he went public after Facebook said it didn’t think the weakness he found was “important” enough to be fixed—fed the tool a list of 65,000 email addresses and watched what happened next.
“As you can see from the output log here, I’m getting a significant amount of results from them,” the researcher said as the video showed the tool crunching the address list. “I’ve spent maybe $10 to buy 200-odd Facebook accounts. And within three minutes, I have managed to do this for 6,000 [email] accounts.”
Ars obtained the video on condition the video not be shared. A full audio transcript appears at the end of this post.
Dropping the ball
In a statement, Facebook said: “It appears that we erroneously closed out this bug bounty report before routing to the appropriate team. We appreciate the researcher sharing the information and are taking initial actions to mitigate this issue while we follow up to better understand their findings.”
A Facebook representative didn’t respond to a question asking if the company told the researcher it didn’t consider the vulnerability important enough to warrant a fix. The representative said Facebook engineers believe they have mitigated the leak by disabling the technique shown in the video.
DataNews instructed public relations people to “frame this as a broad industry issue and normalize the fact that this activity happens regularly.” Facebook has also made the distinction between scraping and hacks or breaches.
It’s not clear if anyone actively exploited this bug to build a massive database, but it certainly wouldn’t be surprising. “I believe this to be quite a dangerous vulnerability, and I would like help in getting this stopped,” the researcher said.
Here’s the written transcript of the video:
So, what I would like to demonstrate here is an active vulnerability within Facebook, which allows malicious users to query, um, email addresses within Facebook and have Facebook return, any matching users.
Um, this works with a front end vulnerability with Facebook, which I’ve reported to them, made them aware of, um, that they do not consider to be important enough to be patched, uh, which I would consider to be quite a significant, uh, privacy violation and a big problem.
This method is currently being used by software, which is available right now within the hacking community.
Currently it’s being used to compromise Facebook accounts for the purpose of taking over pages groups and, uh, Facebook advertising accounts for obviously monetary gain. Um, I’ve set up this visual example within no JS.
What I’ve done here is I’ve taken, uh, 250 Facebook accounts, newly registered Facebook accounts, which I’ve purchased online for about $10.
Um, I have queried or I’m querying 65,000 email addresses. And as you can see from the output log here, I’m getting a significant amount of results from them.
If I have a look at the output file, you can see I have a user ID name and the email address matching the input email addresses, which I have used. Now I have, as I say, I’ve spent maybe $10 using two to buy 200-odd Facebook accounts. And within three minutes, I have managed to do this for 6,000 accounts.
I have tested this at a larger scale, and it is possible to use this to extract feasibly up to 5 million email addresses per day.
Now there was an existing vulnerability with Facebook, uh, earlier this year, which was patched. This is essentially the exact same vulnerability. And for some reason, despite me demonstrating this to Facebook and making them aware of it, um, they have told me directly that they will not be taking action against it.
So I am reaching out to people such as yourselves, uh, in hope that you can use your influence or contacts to get this stopped, because I am very, very confident.
This is not only a huge privacy breach, but this will result in a new, another large data dump, including emails, which is going to allow undesirable parties, not only to have this, uh, email to user ID matches, but to append the email address to phone numbers, which have been available in previous breaches, um, I’m quite happy to demonstrate the front end vulnerability so you can see how this works.
I’m not going to show it in this video simply because I don’t want the video to be, um, I don’t want the method to be exploited, but if I would be quite happy to, to demonstrate it, um, if that is necessary, but as you can see, you can see continues to output more and more and more. I believe this to be quite a dangerous vulnerability and I would like help in getting this stopped.






