
reader comments
63 with 49 posters participating, including story author
As Internet attacks go, data floods designed to knock servers offline are among the crudest, akin to a brutish caveman wielding a club to clobber his rival. Over the years, those clubs have grown ever larger. New data provided by Microsoft on Thursday shows there’s no end in sight to that growth.
The company’s Azure DDoS Protection team said that in November, it fended off what industry experts say is likely the biggest distributed denial-of-service attack ever: a torrent of junk data with a throughput of 3.47 terabits per second. The record DDoS came from more than 10,000 sources located in at least 10 countries around the world.
DDoS arms race
The DDoS targeted an unidentified Azure customer in Asia and lasted for about two minutes.
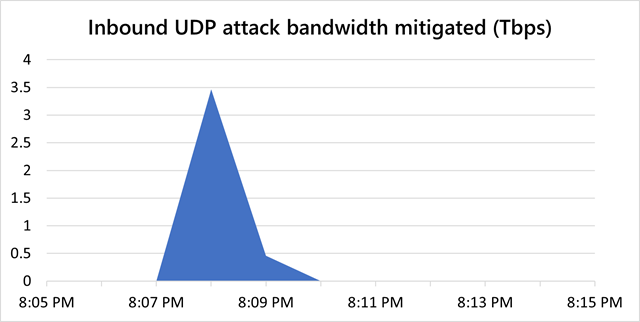
The following month, Microsoft said, Azure warded off two other monster DDoSes. Weighing in at 3.25Tbps, the first one came in four bursts and lasted about 15 minutes.
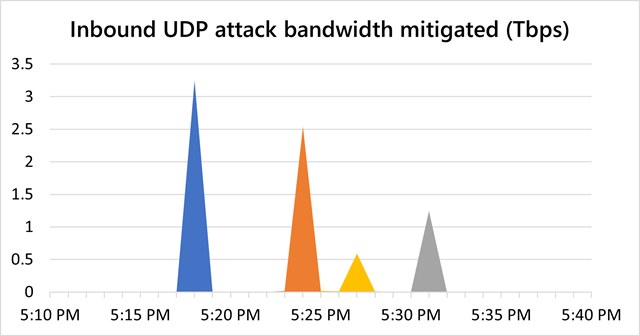
The second December DDoS reached a peak of 2.54Tbps and lasted about five minutes.
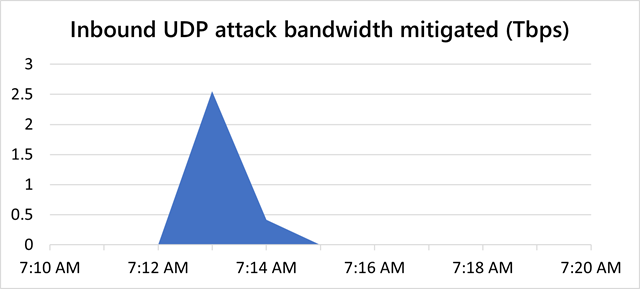 The record beats a 2.5Tbps attack that Microsoft mitigated in the first half of 2021. Previously, one of the biggest attacks was 2.37Tbps in size, a 35 percent increase over a record set in 2018. A separate DDoS in 2020 generated 809 million packets per second, which was also a record at the time.
The record beats a 2.5Tbps attack that Microsoft mitigated in the first half of 2021. Previously, one of the biggest attacks was 2.37Tbps in size, a 35 percent increase over a record set in 2018. A separate DDoS in 2020 generated 809 million packets per second, which was also a record at the time.
Packet-per-second DDoSes work by exhausting the computing resources of a server. More traditional volumetric attacks, by contrast, consume available bandwidth either inside the targeted network or service or get between the target and the rest of the Internet. The 3.7Tbps attack delivered roughly 340 million packets per second.
reflection amplification attacks. In this kind of attack, malefactors point their data cannons at a misconfigured Internet device in a way that causes the device to redirect a much bigger payload to the ultimate target. This latter method is primarily what’s driving the ever-growing DDoS arms race.
DDoSers regularly discover new amplification vectors. In 2014, attacks that abused the Internet’s Network Time Protocol, or NTP, came into vogue when the protocol was leveraged to knock servers belonging to Steam, Origin, Battle.net, EA, and other big game makers offline. This method facilitates a 206-fold increase in throughput, meaning a gigabyte of data delivered by an end device reaches 206 gigabytes by the time it reaches its final target.
In 2018, scofflaws turned to memcachd, a database caching system for speeding up websites and networks. The memcached amplifier can deliver attacks that are as much as 51,000 times their original size, making it by far the biggest amplification method ever to be used in the wild. A year later, DDoSes were reflected off devices using WS-Discovery, a protocol found in a wide array of network-connected cameras, DVRs, and other Internet-of-Things devices.
More recently, DDoSers have abused Microsoft RDP, and they’ve misconfigured servers running CLDAP (short for Connectionless Lightweight Directory Access Protocol) and the Plex Media Server when it runs the Simple Service Discovery Protocol (or SSDP). This can expose devices to the general Internet.






