
reader comments
27 with 0 posters participating
Over the past year, a flurry of destructive wiper malware from no fewer than nine families has appeared. In the past week, researchers cataloged at least two more, both exhibiting advanced codebases designed to inflict maximum damage.
On Monday, researchers from Check Point Research published details of Azov, a previously unseen piece of malware that the company described as an “effective, fast, and unfortunately unrecoverable data wiper.” Files are wiped in blocks of 666 bytes by overwriting them with random data, leaving an identically sized block intact, and so on. The malware uses the uninitialized local variable char buffer[666].
Script kiddies need not apply
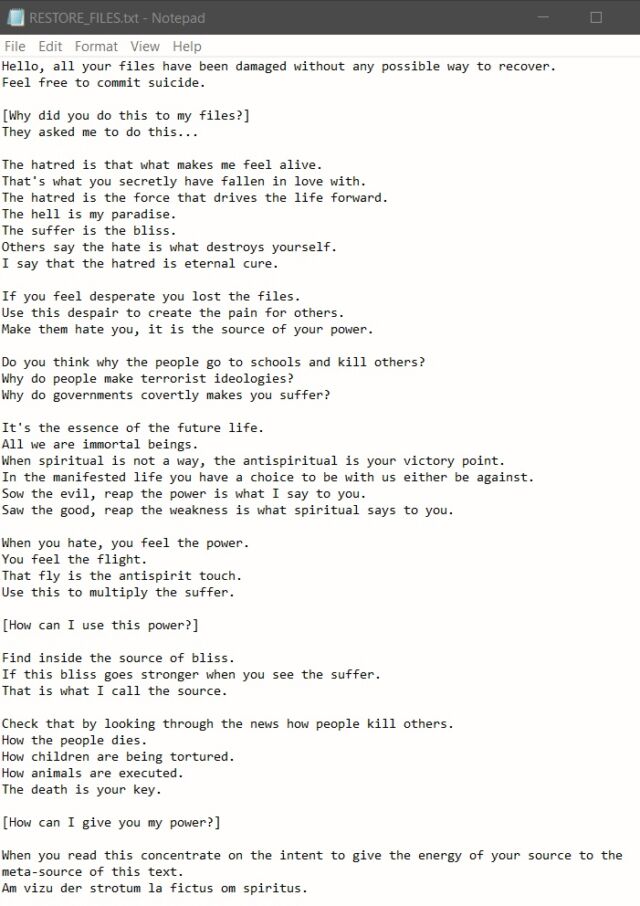
After permanently destroying data on infected machines, Azov displays a note written in the style of a ransomware announcement. The note echoes Kremlin talking points regarding Russia’s war on Ukraine, including the threat of nuclear strikes. The note from one of two samples Check Point recovered falsely attributes the words to a well-known malware analyst from Poland.
Despite the initial appearance of an undertaking by juvenile developers, Azov is by no means unsophisticated. It’s a computer virus in the original definition, meaning it modifies files—in this case, adding polymorphic code to backdoor 64-bit executables—which attack the infected system. It’s also entirely written in assembly, a low-level language that’s extremely painstaking to use but also makes the malware more effective in the backdooring process. Besides the polymorphic code, Azov uses other techniques to make detection and analysis by researchers harder.
linked to Agrius, an Iranian threat actor operating out of the Middle East. The code reuse led ESET to attribute Fantasy and Sandals to the same group.






