
reader comments
13 with
Hackers working on behalf of the North Korean government have pulled off a massive supply chain attack on Windows and macOS users of 3CX, a widely used voice and video calling desktop client, researchers from multiple security firms said.
The attack compromised the software build system used to create and distribute Windows and macOS versions of the app, which provides both VoIP and PBX services to “600,000+ customers,” including American Express, Mercedes-Benz, and Price Waterhouse Cooper. Control of the software build system gave the attackers the ability to hide malware inside 3CX apps that were digitally signed using the company’s official signing key. The macOS version, according to macOS security expert Patrick Wardle, was also notarized by Apple, indicating that the company analyzed the app and detected no malicious functionality.
In the making since 2022
“This is a classic supply chain attack, designed to exploit trust relationships between an organization and external parties,” Lotem Finkelstein, Director of Threat Intelligence & Research at Check Point Software, said in an email. “This includes partnerships with vendors or the use of a third-party software which most businesses are reliant on in some way. This incident is a reminder of just how critical it is that we do our due diligence in terms of scrutinizing who we conduct business with.”
Security firm CrowdStrike said the infrastructure and an encryption key used in the attack match those seen in a March 7 campaign carried out by Labyrinth Chollima, the tracking name for a threat actor aligned with the North Korean government.
spike in behavioral detections of the 3CXDesktopApp. That same day, 3CX users started online threads discussing what they believed were potential false-positive detections of 3CXDesktopApp by their endpoint security apps.
3CX Chief Information Security Officer Pierre Jourdan has confirmed that the Electron Windows App with version numbers 18.12.407 and 18.12.416 and the Electron Mac App versions 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 include a “security issue.” He said the payloads were inserted into bundled libraries compiled through Git, a system that software developers use to track changes in the apps they produce. Many of the attacker-controlled servers that infected machines reach out to have already been shut down, he added.
Poisoning the well
The incident is reminiscent of a supply chain attack detected in December 2020 that hit users of SolarWinds network management software. The US government and multiple security researchers attributed the attack to Cozy Bear, one of the tracking names for a hacking group believed to be part of the Russian Federal Security Service (FSB). As is the case with 3CX, the SolarWinds hackers compromised the company’s software build system and used it to distribute a backdoored update to roughly 18,000 customers. About 100 of them received follow-on hacks that used the backdoor to install a second-stage payload. Victims included tech companies Malwarebytes, FireEye, and Microsoft; 10 US government agencies, including the Departments of Justice, Commerce, Treasury, Energy, and Homeland Security, and think tanks and NGOs, making the hacking campaign among the worst in modern US history.
Preliminary analysis from Symantec indicates the compromised installers for Windows and Mac contain clean versions of the app with all of their normal functionality, preventing end users from suspecting anything is amiss. The attackers added an additional payload through a technique known as DLL Sideloading, which adds malicious functionality, Sophos said.
CrowdStrike said. In a few cases, the attackers carried out “hands-on-keyboard activity” on infected machines.
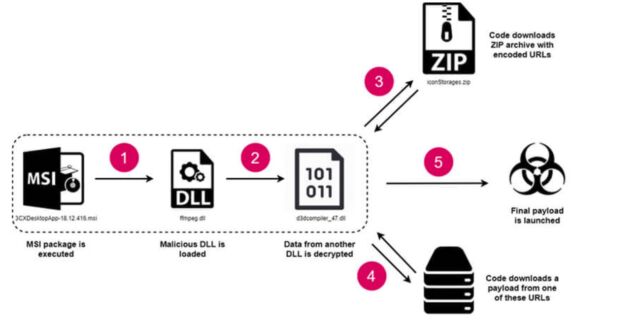
In the case of the Trojanized Windows versions, researchers from CheckPoint said, the attackers used an MSI executable signed with 3CX’s key to load a malicious file named ffmmpeg.dll. The file was modified to read encrypted data from another file named d3dcompiler_47.dll. This latter file pulled an encoded list of URLs the attackers stored in a GitHub archive. The DLL file then used the list to download and run a final payload from one of the URLs.
“The important point about communication with GitHub is that the delay of one week is set in the code before the request to GitHub actually occurs,” CheckPoint researchers wrote. “After this step is finally accomplished, the final payload is downloaded from one of these URLs and executed.”
CheckPoint provided the following illustration of the Windows infection chain:
Any organization that uses 3CX should immediately begin analyzing its network infrastructure to look for signs of compromise. CrowdStrike recommends that all 3CX users at least temporarily stop using the software while investigations are pending. Sophos provided a script that will determine whether networks have communicated with threat actor infrastructure. Sophos and other firms have also published domains, file hashes, and other indicators of compromise that 3CX users can use.






