
Enlarge (credit: Getty Images)
lost mode for iPhones, which prevent a lost or stolen device from being used without entering its passcode.
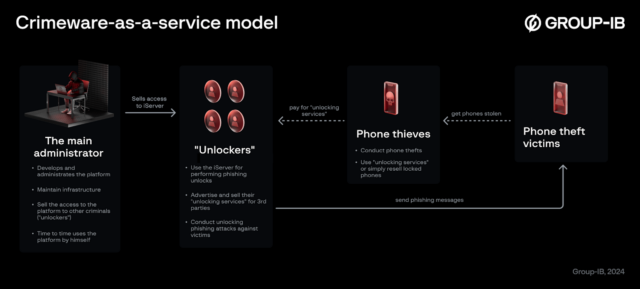

iServer’s phishing-as-a-service model. (credit: Group-IB)
Catering to low-skilled thieves
An international operation coordinated by Europol’s European Cybercrime Center said it arrested the Argentinian national that was behind iServer and identified more than 2,000 “unlockers” who had enrolled in the phishing platform over the years. Investigators ultimately found that the criminal network had been used to unlock more than 1.2 million mobile phones. Officials said they also identified 483,000 phone owners who had received messages phishing for credentials for their lost or stolen devices.
Read 7 remaining paragraphs | Comments
Article Tags:
featuredArticle Categories:
Technology





