 reader comments
reader comments
19 with 18 posters participating
Multiple unsecured entry points allowed researchers to access data belonging to Fermilab, a national particle physics and accelerator lab supported by the Department of Energy.
This week, security researchers Robert Willis, John Jackson, and Jackson Henry of the Sakura Samurai ethical hacking group have shared details on how they were able to get their hands on sensitive systems and data hosted at Fermilab.
After enumerating and peeking inside the fnal.gov subdomains using commonly available tools like amass, dirsearch, and nmap, the researchers discovered open directories, open ports, and unsecured services that attackers could have used to extract proprietary data.
A naked FTP server
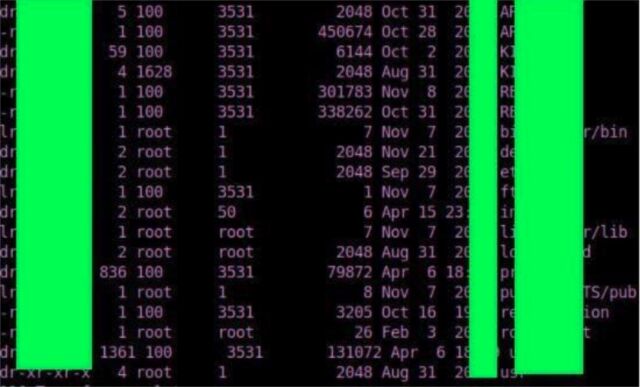
The server exposed configuration data for one of Fermilab’s experiments called “NoVa,” which concerns studying the purpose of neutrinos in the evolution of the cosmos.
The researchers discovered that one of the tar.gz archives hosted on the FTP server contained Apache Tomcat server credentials in plaintext:

The researchers verified that the credentials were valid at the time of their discovery but ceased experimenting further so as to keep their research efforts ethical.
Thousands of documents and project tickets exposed
Likewise, in another set of unrestricted subdomains, the researchers found over 4,500 tickets used for tracking Fermilab’s internal projects. Many of these contained sensitive attachments and private communications.
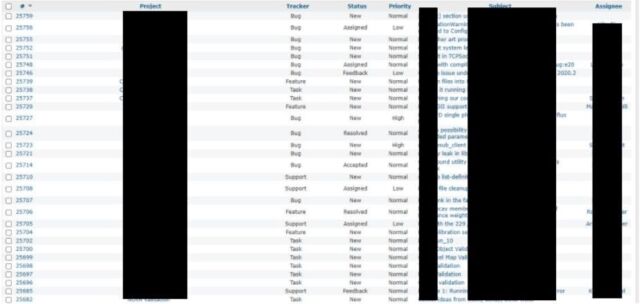
And yet another server ran a web application that listed the full names of users registered under different workgroups, along with their email addresses, user IDs, and other department-specific information.
Ferminab’s vulnerability disclosure policy. Fermilab was quick to respond to the researchers’ initial report and squashed the bugs swiftly.
“Fermilab managed the interactions regarding the findings in a quick and positive way. They didn’t question the authenticity of our vulnerabilities and immediately dug in and patched—acknowledging the sense of urgency,” Jackson said. “The first thought that we had was about the possibility of a nation-state threat actor acquiring this data, especially because it’s no surprise that Fermilab works on groundbreaking scientific research.”
“We knew we had to act quickly and inform Fermilab. Nonetheless, still crazy to see the ease in which we acquired sensitive data, which included credentials to scientific equipment and servers,” he added.
This discovery of a US government-funded national lab having serious security flaws that are trivial to exploit comes as multiple US federal agencies continue to be targets of cyberattacks.
Just last week, Ars reported that threat actors had potentially hacked at least five US government agencies via Pulse Connect Secure VPN vulnerabilities. Separately, the FBI is investigating an extortion attempt by ransomware operators against the Metropolitan Police Department in Washington, DC.
Fermilab declined to comment.
The researchers’ detailed findings related to the research are provided in their blog post.
Ax Sharma is a security researcher, engineer, and reporter who publishes in leading publications. His expertise lies in malware research, reverse engineering, and application security. He’s an active community member of the OWASP Foundation and the British Association of Journalists.






