 reader comments
reader comments
84 with 57 posters participating
A code execution bug in Apple’s macOS allows remote attackers to run arbitrary commands on your device. And the worst part is, Apple hasn’t fully patched it yet, as tested by Ars.
Those shortcut files can take over your Mac
Independent security researcher Park Minchan has discovered a vulnerability in the macOS that lets threat actors execute commands on your computer. Shortcut files that have the inetloc extension are capable of embedding commands inside. The flaw impacts macOS Big Sur and prior versions.
“A vulnerability in the way macOS processes inetloc files causes it to run commands embedded inside, the commands it runs can be local to the macOS allowing the execution of arbitrary commands by the user without any warning / prompts,” explains Minchan. “Originally, inetloc files are shortcuts to an Internet location, such as an RSS feed or a telnet location; and contain the server address and possibly a username and password for SSH and telnet connections; can be created by typing a URL in a text editor and dragging the text to the Desktop.”
Minchan reported the flaw to Apple via the SSD Secure Disclosure program as mentioned in the writeup.
Internet shortcuts are present in both Windows and macOS systems. But this specific bug adversely impacts macOS users, especially those who use a native email client like the “Mail” app.
For example, opening an email that contains an inetloc attachment via the “Mail” app will trigger the vulnerability without warning. In the test email below is an attached shortcut file “test.inetloc,” clicking on which launches the Calculator app on macOS:
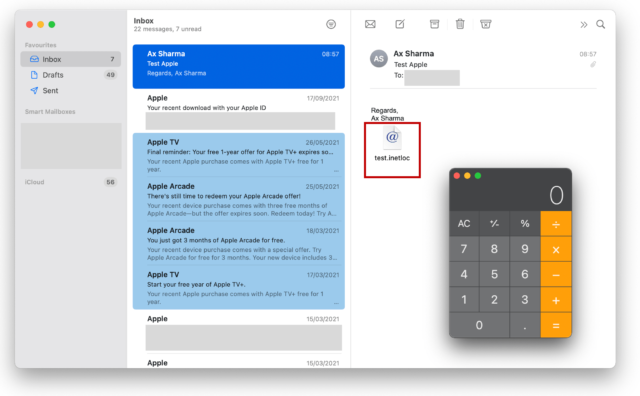
Apple’s “fix” can easily be bypassed
The cause of the vulnerability is rather simple. An Internet shortcut file typically contains a URL. But, what happens if one includes a “file://” URL?
URLs beginning with “file://” rather than commonly seen “http://” or “https://” are used to retrieve files from within one’s own computer system. You can try doing this on your Mac now. Opening a local file on your computer with the Chrome or Safari web browser will automatically generate its equivalent file:// location in the address bar. And, Internet shortcuts or inetloc files can be easily crafted to point to “file://” URLs as opposed to HTTP ones.
Although Apple was notified of the flaw and, starting with Big Sur, blocks the inclusion of file:// URLs in Internet shortcuts, one can get around the block by changing the text case:
“Newer versions of macOS (from Big Sur) have blocked the file:// prefix (in the com.apple.generic-internet-location) however they did a case matching causing File:// or fIle:// to bypass the check,” explains Minchan.
I tested this theory on my macOS Big Sur 11.3.1 and 11.6 using the proof-of-concept (PoC) code provided by Minchan and can confirm the bug has indeed not been fully patched:
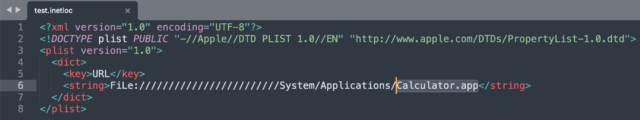
This snippet with just eight lines of code is what launched the Calculator shown above. But any skillful threat actor could modify this test code to execute outright malicious code on the victim’s machine. For example, Ars noticed more advanced payloads like “FiLe:///////////////bin/pwd” ran successfully.
Apple Mac users are warned to be cautious when opening .inetloc Internet shortcuts, especially ones that come in via email attachments.






