
reader comments
92 with
Phishing mongers have released a torrent of image-based junk emails that embed QR codes into their bodies to successfully bypass security protections and provide a level of customization to more easily fool recipients, researchers said.
In many cases, the emails come from a compromised email address inside the organization the recipient works in, a tactic that provides a false sense of authenticity, researchers from security firm Inky said. The emails Inky detected instruct the employee to resolve security issues such as a missing two-factor authentication enrollment or to change a password and warn of repercussions that may occur if the recipient fails to follow through. Those who take the bait and click on the QR code are led to a site masquerading as a legitimate one used by the company but it captures passwords and sends them to the attackers.
Inky described the campaign’s approach as “spray and pray” because the threat actors behind it send the emails to as many people as possible to generate results.
There are a few things that make this campaign stand out. First, the emails contain no text. Instead, they have only an attached image file. This allows the emails to escape notice by security protections that analyze the text-based words sent in an email. Some email programs and services, by default, automatically display attached images directly in the body, with some providing no way to suppress them. Recipients then often don’t notice that the image-based email contains no text.
Another distinguishing feature: the images embed a QR code that leads to the credential-harvesting site. This can reduce the time it takes to visit the site and lower the chance the employee will realize something is amiss. The QR codes also cause the loaded website to prefill the recipient’s unique email address in the username field. This adds another false sense of assurance that the email and site are legitimate.
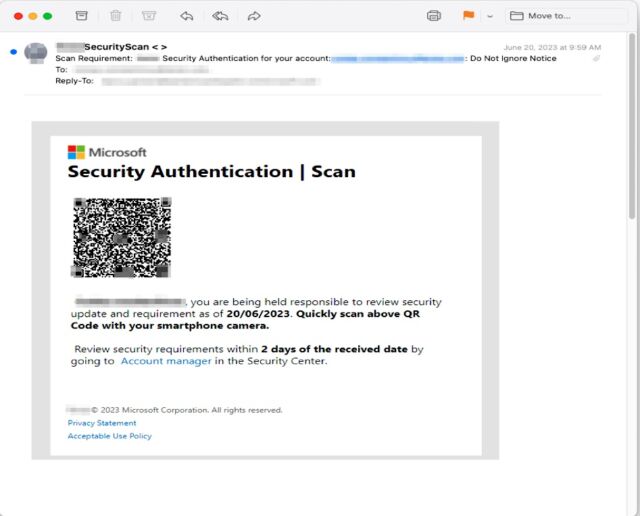
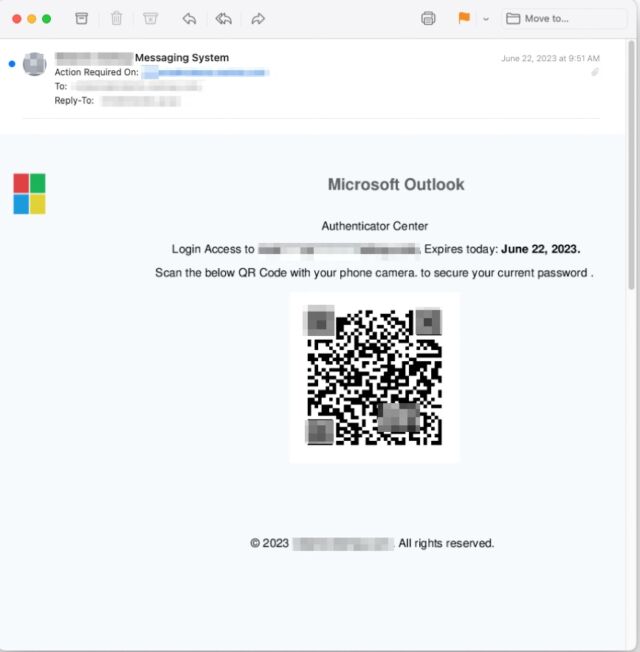
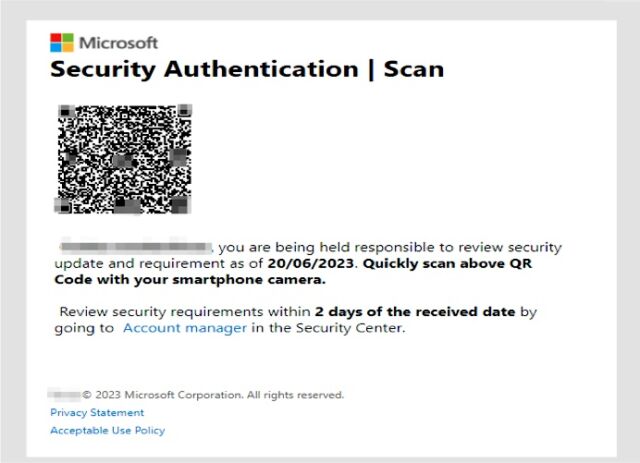
In a writeup published Friday, the Inky researchers wrote:
according to AGG IT Services, and one in four people reporting they have clicked on a phishing email at work, according to Tessian, people underestimate the costs of phishing at their own peril.





