
reader comments
2 with 2 posters participating
Google is adding its password checkup feature to Android, making the mobile OS the latest company offering to give users an easy way to check if the passcodes they’re using have been compromised.
Password Checkup works by checking credentials entered into apps against a list of billions of credentials compromised in the innumerable website breaches that have occurred in recent years. In the event there’s a match, users receive an alert, along with a prompt that can take them to Google’s password manager page, which offers a way to review the security of all saved credentials.
Alerts look like this:
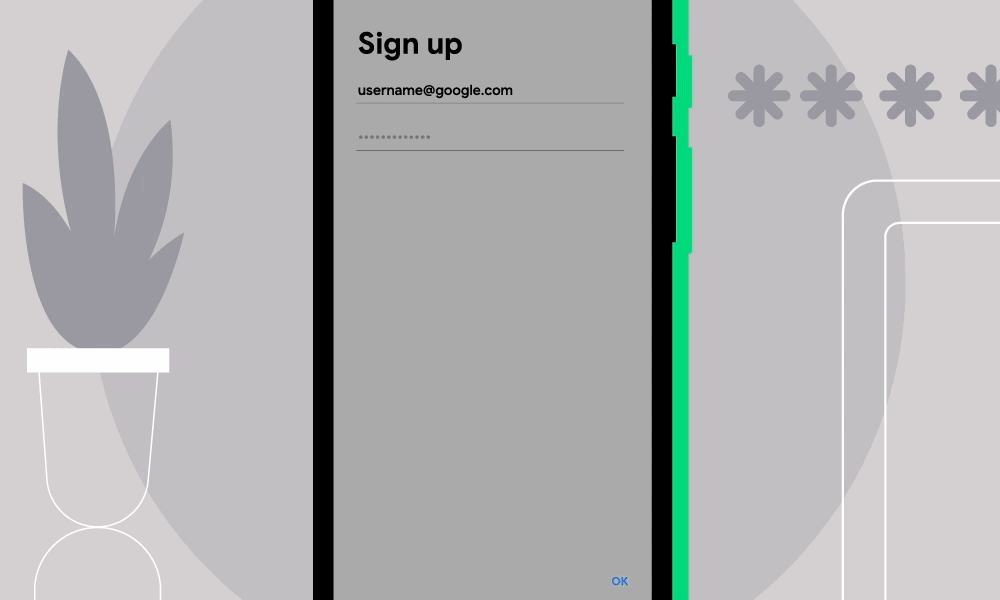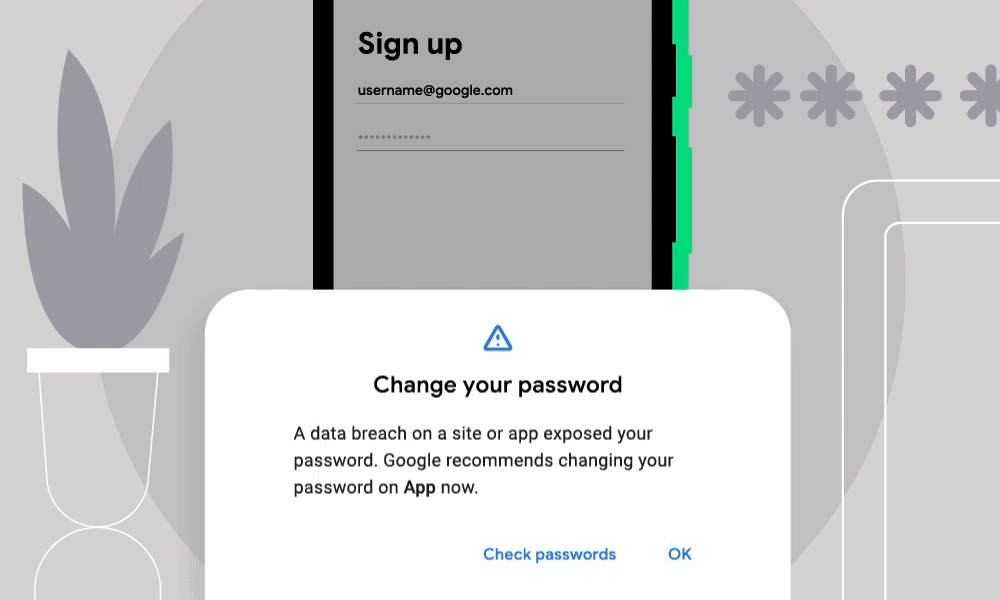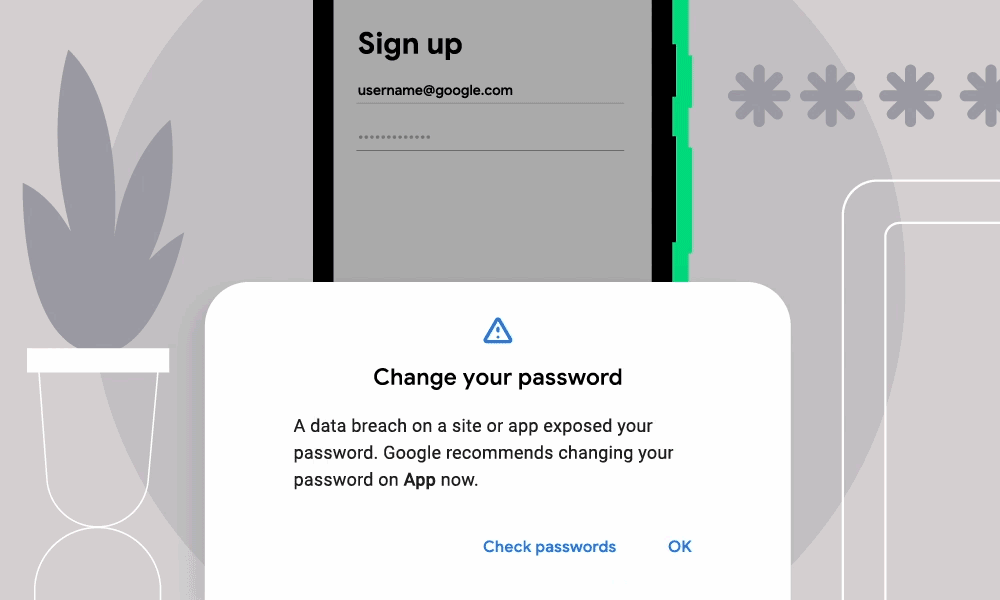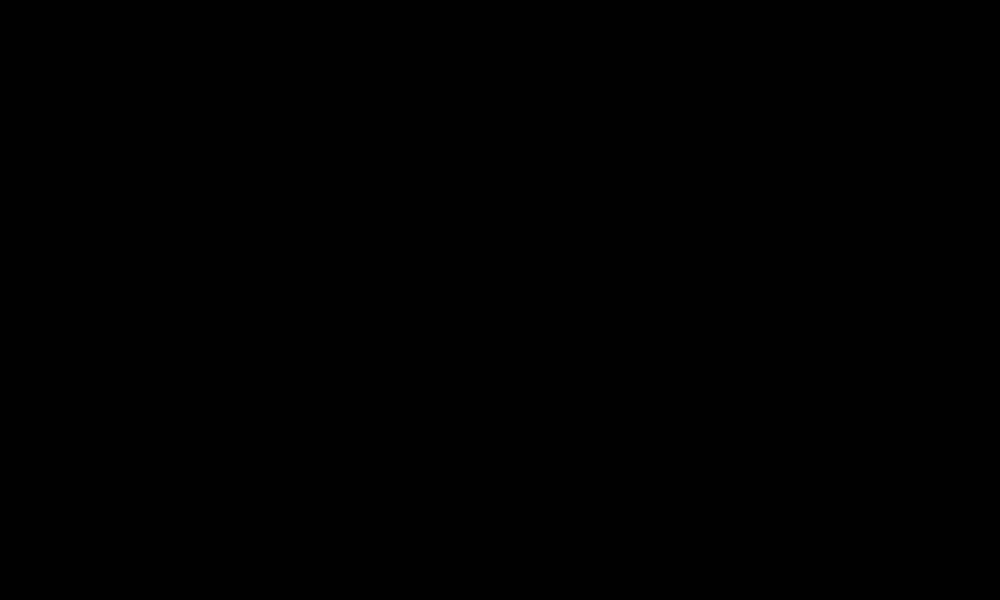 Google introduced Password Checkup in early 2019, in the form of a Chrome extension. In October of that year, the feature made its way into the Google Password Manager, a dashboard that examines Web passwords saved within Chrome that are synchronized using a Google account. Two months later, the company added it to Chrome.
Google introduced Password Checkup in early 2019, in the form of a Chrome extension. In October of that year, the feature made its way into the Google Password Manager, a dashboard that examines Web passwords saved within Chrome that are synchronized using a Google account. Two months later, the company added it to Chrome.
Google’s Password Manager makes it easy for users to directly visit sites using bad passwords by clicking the “Change Password” button displayed next to each compromised or weak password. The password manager is accessible from any browser, but it works only when users sync credentials using their Google account password, rather than an optional standalone password.
The new password checkup was available as of Tuesday on Android 9 and above for users of autofill with Android, a feature that automatically adds passwords, addresses, payment details, and other information commonly entered into Web and app forms.
post published Tuesday, Google said that the implementation ensures that:
- Only an encrypted hash of the credential leaves the device (the first two bytes of the hash are sent unencrypted to partition the database)
- The server returns a list of encrypted hashes of known breached credentials that share the same prefix
- The actual determination of whether the credential has been breached happens locally on the user’s device
- The server (Google) does not have access to the unencrypted hash of the user’s password and the client (User) does not have access to the list of unencrypted hashes of potentially breached credentials
Google has written more about how the implementation works here.
On most Android devices, autofill can be enabled by:
- Opening Settings
- Tapping System > Languages & input > Advanced
- Tapping Autofill service
- Tapping Google to make sure the setting is enabled
Separately, Google on Tuesday reminded users of two other security features added to Android autofill last September. The first is a password generator that will automatically choose a strong and unique password and save it to users’ Google accounts. The generator can be accessed by long-pressing the password field and selecting Autofill in the pop-up menu.
Users can also configure the Android autofill to require biometric authentication before it will add credentials or payment information to an app or Web field. Biometric authentication can be enabled inside of the Autofill with Google settings.





