
reader comments
43 with 35 posters participating, including story author
The Lithuanian National Cyber Security Centre (NCSC) recently published a security assessment of three recent-model Chinese-made smartphones—Huawei’s P40 5G, Xiaomi’s Mi 10T 5G, and OnePlus’ 8T 5G. Sufficiently determined US shoppers can find the P40 5G on Amazon and the Mi 10T 5G on Walmart.com—but we will not be providing direct links to those phones, given the results of the NCSC’s security audit.
The Xiaomi phone includes software modules specifically designed to leak data to Chinese authorities and to censor media related to topics the Chinese government considers sensitive. The Huawei phone replaces the standard Google Play application store with third-party substitutes the NCSC found to harbor sketchy, potentially malicious repackaging of common applications.
The OnePlus 8T 5G—arguably, the best-known and most widely marketed phone of the three—was the only one to escape the NCSC’s scrutiny without any red flags raised.
Xiaomi Mi 10T 5G

Xiaomi’s Mi 10T 5G ships with a nonstandard browser called “Mi Browser.” The NCSC found two components in Mi Browser which it didn’t like—Google Analytics, and a less familiar module called Sensor Data.
The Google Analytics module in Mi Browser can read from the device’s browsing and search history and can then send that data to Xiaomi servers for unspecified analysis and use. The Google Analytics module is activated automatically by default during the phone’s first activation or after any factory reset.
excessive data collection and abuse of user privacy.
The NCSC also found that the user’s mobile phone number is silently registered to servers in Singapore via encrypted SMS message on activation of default Xiaomi cloud services. The mobile phone number is sent whether the user ties it to a new cloud account or not, and the encrypted SMS is not visible to the user.
Several of the Xiaomi system applications on the Mi 10T 5G regularly download a file called MiAdBlackListConfig from servers in Singapore. In this file, the NCSC found 449 records identifying religious, political, and social groups. Software classes in these Xiaomi applications use MiAdBlackListConfig to analyze multimedia which might be displayed on the device and block that content if “undesirable” keywords are associated with it.
Although the NCSC discovered that the actual content filtering via MiAdBlackListConfig is disabled on phones registered in the European Union, the phones still regularly download the blocklist itself—and, the agency says, can be remotely reactivated at any time.
Huawei P40 5G
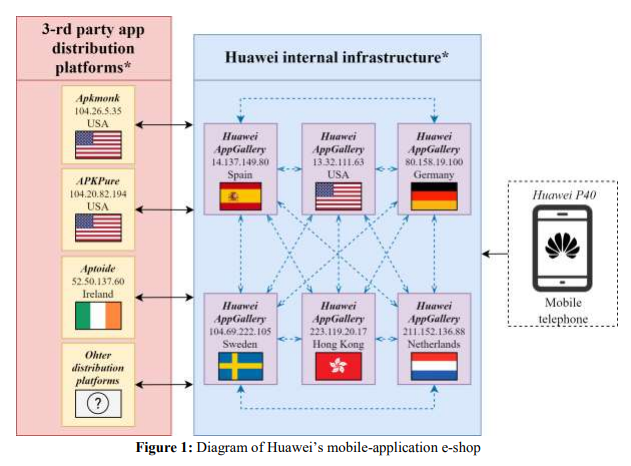
Although the NCSC did not find the same class of spyware and content-filtering modules in Huawei’s P40 5G as it had in the Mi 10T 5G, it still wasn’t happy with the phone’s software infrastructure—and for good reason.
The P40 5G’s most obvious problems stem from its replacement of Google’s Play Store with Huawei’s own AppGallery store, which it bills as “a safer place to get all your favorite apps.” The NCSC found that, if a user searches AppGallery for a particular application, they will be silently redirected to third-party app stores if no match is found in AppGallery itself.
All in One social media, CNC Machinist Tapping Calculator, and “Messenger app, Light All-in-One, Live Free Chat Pro App.”
We’re not certain how much salt to take with the NCSC’s specific “malware” findings since the agency did not reverse engineer any of the three apps VirusTotal didn’t like—and antivirus false positives on less well-known apps happen with some regularity. However, the apparently silent linking from AppGallery to third-party app stores does introduce a genuine risk of device compromise.
Although Apkmonk, APKPure, and Aptoide are all reasonably well-known “alternate stores,” they’re less thoroughly curated than Google’s own Play Store. Aptoide, for example, offers both its own main repository—which is curated, scanned, and appears to be as safe as the Play Store. But Aptoide also allows easy self-hosting of APK repositories for anyone who wants to upload their own—whether they’re a user wanting to “back up” APKs which could disappear from the Play Store, or a developer hosting their own original software.
The ease of repository creation on Aptoide—and the prevalence of pirated and cracked apps on its user repositories—makes incautious “shopping” by less-informed users a severe security risk, particularly when those users might not realize they’ve left the safety of the mainstream in the first place.
Even users not looking for pirated software may inadvertently stumble on malware-added repackaging or copycat versions of legitimate applications, with apparent “legitimacy” added by re-signing the modified or copycat application with the uploader’s own key.
Conclusions
Based on the NCSC’s findings, there doesn’t seem to be any issue with the OnePlus phone—which comes as little surprise, as it’s the only brand of the three which hasn’t come under repeated, negative scrutiny from non-Chinese administrations.
Particularly adventurous and/or Google-hating consumers might reasonably be interested in Huawei’s P40, which seems afflicted more with a lack of malware-preventing guardrails than with actual directly imposed censorship and/or spyware.
Finally, we’d strongly advise avoiding the Xiaomi Mi 10T—its deactivated but regularly updated blocklist functionality strikes us as a warning of direct authoritarian oversight which should not be lightly ignored.






