
reader comments
115 with 92 posters participating, including story author
When we teach people how to avoid falling victim to phishing sites, we usually advise closely inspecting the address bar to make sure it does contain HTTPS and that it doesn’t contain suspicious domains such as google.evildomain.com or substitute letters such as g00gle.com. But what if someone found a way to phish passwords using a malicious site that didn’t contain these telltale signs?
One researcher has devised a technique to do just that. He calls it a BitB, short for “browser in the browser.” It uses a fake browser window inside a real browser window to spoof an OAuth page. Hundreds of thousands of sites use the OAuth protocol to let visitors login using their existing accounts with companies like Google, Facebook, or Apple. Instead of having to create an account on the new site, visitors can use an account that they already have—and the magic of OAuth does the rest.
Exploiting trust
The photo editing site Canva, for instance, gives visitors the option to login using any of three common accounts. The images below show what a user sees after clicking the “sign in” button; following that, the image show what appears after choosing to sign in with a Google password. After the user chooses Google, a new browser window with a legitimate address opens in front of the existing Canva window.
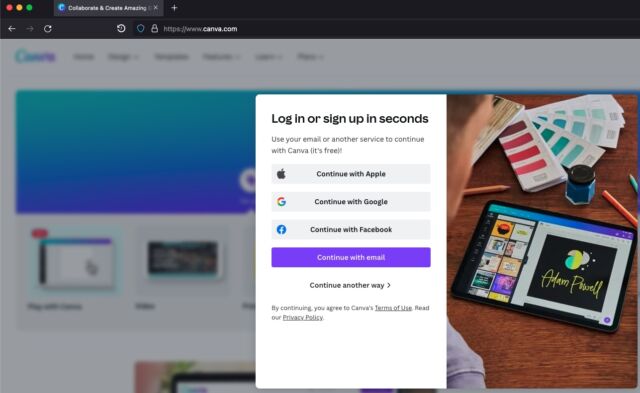
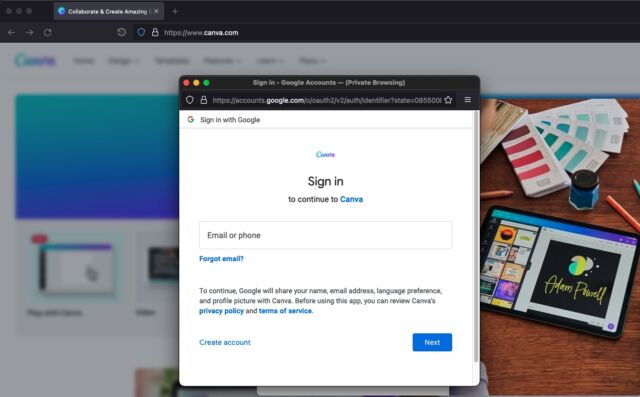
The OAuth protocol ensures that only Google receives the user password. Canva never sees the credentials. Instead, OAuth securely establishes a login session with Google and, when the username and password check out, Google provides the visitor with a token that gives access to Canva. (Something similar happens when a shopper chooses a payment method like PayPal.)
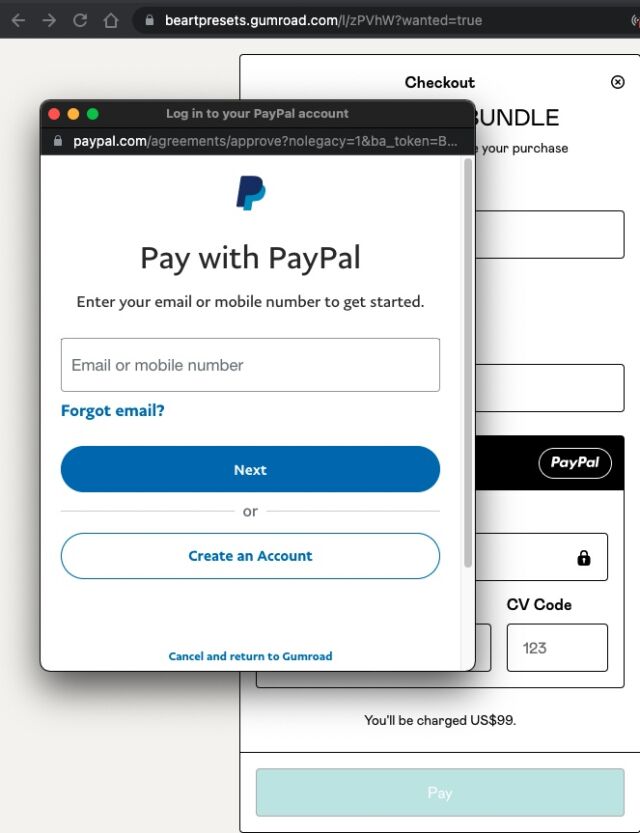
The BitB technique capitalizes on this scheme. Instead of opening a genuine second browser window that’s connected to the site facilitating the login or payment, BitB uses a series of HTML and cascading style sheets (CSS) tricks to convincingly spoof the second window. The URL that appears there can show a valid address, complete with a padlock and HTTPS prefix. The layout and behavior of the window appear identical to the real thing.
A researcher using the handle mr.d0x described the technique last week. His proof-of-concept exploit starts with a Web page showing a painstakingly accurate spoofing of Canva. In the event a visitor chooses to login using Apple, Google, or Facebook, the fake Canva page opens a new page that embeds what looks like the familiar-looking OAuth page.

This new page is also a spoof. It includes all the graphics a person would expect to see when using Google to login. The page also has the legitimate Google address displayed in what appears to be the address bar. The new window behaves much like a browser window would if connected to a real Google OAuth session.
If a potential victim opens the fake Canva.com page and tries to login with Google, “it will open a new browser window and go to [what appears to be] the URL accounts.google.com,” mr.d0x wrote in a message. In actuality, the fake Canva site “doesn’t open a new browser window. It makes it LOOK like a new browser window was opened but it’s only HTML/CSS. Now that fake window sets the URL to accounts.google.com, but that’s an illusion.”
Malvertisers: please don’t read this
A fellow security researcher was impressed enough by the demonstration to create a YouTube video that more vividly shows what the technique looks like. It also explains how the technique works and how easy it is to carry out.
here.)
“This browser-in-the-browser attack is perfect for phishing,” one developer wrote. “If you’re involved in malvertising, please don’t read this. We don’t want to give you ideas.”
“Ooh that’s nasty: Browser In The Browser (BITB) Attack, a new phishing technique that allows stealing credentials that even a web professional can’t detect,” another person said.
The technique has been actively used in the wild at least once before. As security firm Zscaler reported in 2020, scammers used a BitB attack in an attempt to steal credentials for video game distribution service Steam.
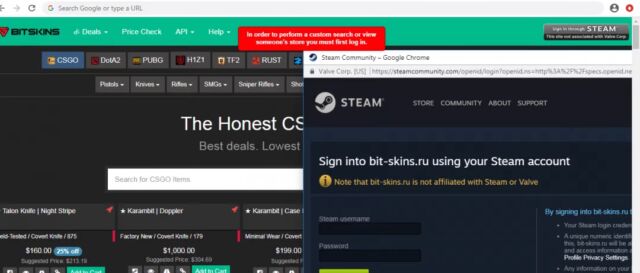
While the method is convincing, it has a few weaknesses that should give savvy visitors a foolproof way to detect that something is amiss. Genuine OAuth or payment windows are in fact separate browser instances that are distinct from the primary page. That means a user can resize them and move them anywhere on the monitor, including outside the primary window.
BitB windows, by contrast, aren’t a separate browser instance at all. Instead, they’re images rendered by custom HTML and CSS and contained in the primary window. That means the fake pages can’t be resized, fully maximized or dragged outside the primary window.
Unfortunately, as mr.d0x pointed out, these checks might be difficult to teach “because now we move away from the ‘check the URL’” advice that’s standard. “You’re teaching users to do something they never do.”
All users should protect their accounts with two-factor authentication. One other thing more experienced users can do is right click on the popup page and choose “inspect.” If the window is a BitB spawn, its URL will be hardcoded into the HTML.
It wouldn’t be surprising to find that the BitB technique has been more widely used, but the reaction mr.d0x received demonstrates that many security defenders aren’t aware of BitB. And that means plenty of end users aren’t, either.






